Hi, In my previous post, I
- Installed NSX-T
- Add Compute manager
- Add the Second NSX-T Manager appliance
- Add the Third NSX-T Manager appliance
- Set NSX-T Manager Virtual IP address
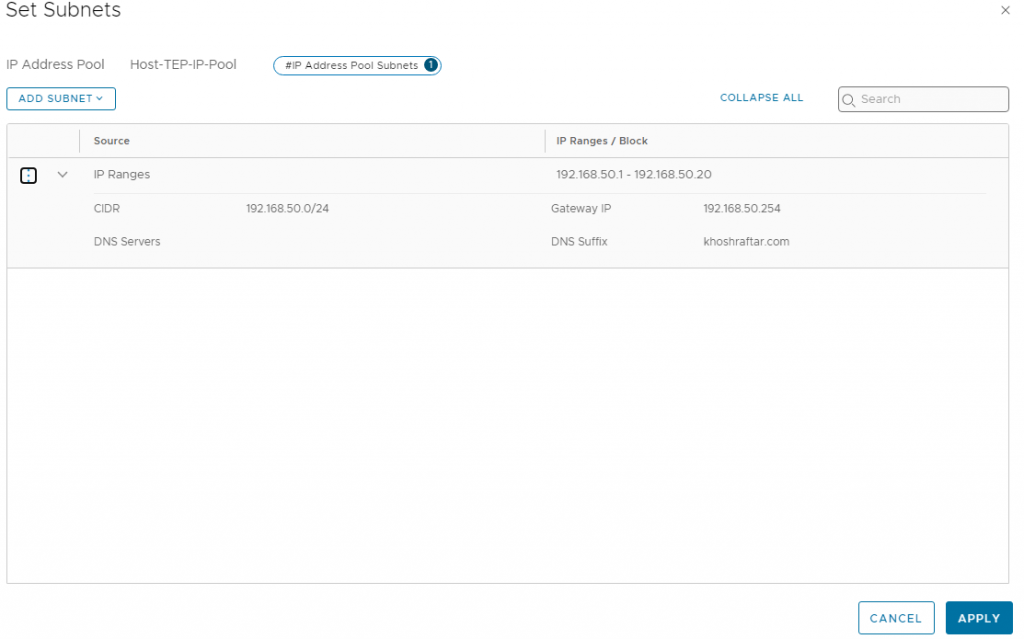
- Add IP Address Pool
- Add Uplink Profiles
- Add Transport Zones
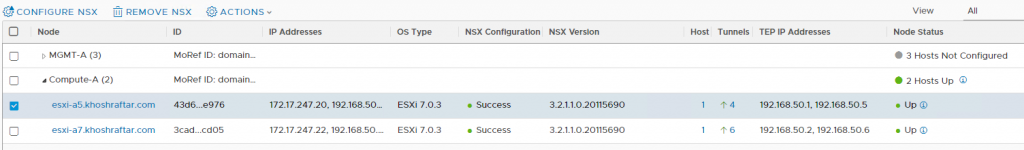
- Prepare Host Transport Nodes
- Add Segment
- Install NSX Edge1
- Install NSX Edge2
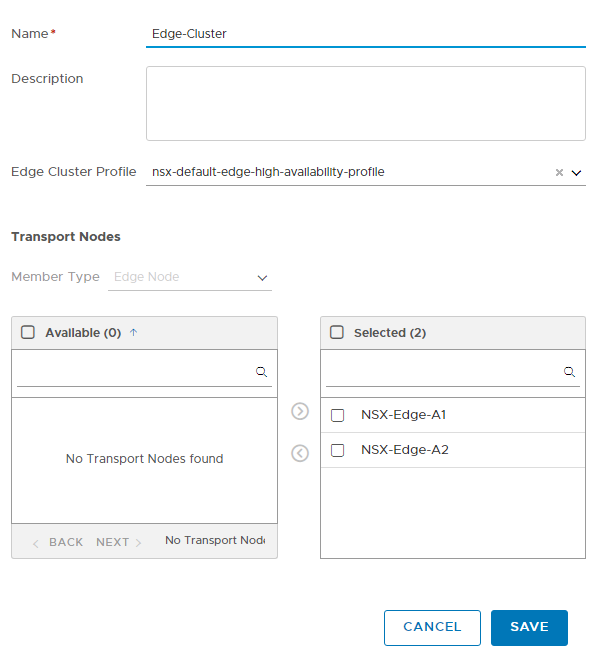
- Add Edge Cluster
- Add Tier-1 Gateways
In the NSX-T. Now, I want to Add Tier-0 Gateways.
A tier-0 gateway has downlink connections to tier-1 gateways and external connections to physical networks.
You can configure the HA (high availability) mode of a tier-0 gateway to be active-active or active-standby. The following services are only supported in active-standby mode:
- NAT
- Load balancing
- Stateful firewall
- VPN
Tier-0 and tier-1 gateways support the following addressing configurations for all interfaces (external interfaces, service interfaces, and downlinks) in both single-tier and multi-tiered topologies.
Note:
You can configure the tier-0 gateway to support EVPN (Ethernet VPN).
1- Go to the Networking –> Connectivity –> Tier-0 Gateways –> Add Gateway –> Click Add Tier-0 Gateway.

2- Enter a name for the gateway.
3- Select an HA (high availability) mode.
The default mode is active-active. In the active-active mode, traffic is load balanced across all members. In active-standby mode, all traffic is processed by an elected active member. If the active member fails, a new member is elected to be active.
4- If the HA mode is active-standby, select a failover mode.
| Option | Description |
|---|---|
| Preemptive | If the preferred node fails and recovers, it will preempt its peer and become the active node. The peer will change its state to standby. |
| Non-preemptive | If the preferred node fails and recovers, it will check if its peer is the active node. If so, the preferred node will not preempt its peer and will be the standby node. |
5- (Optional) Select an NSX Edge cluster.
6- (Optional) Click Additional Settings
- In the Internal Transit Subnet field, enter a subnet. This is the subnet used for communication between components within this gateway. The default is 169.254.0.0/24.
- In the T0-T1 Transit Subnets field, enter one or more subnets. These subnets are used for communication between this gateway and all tier-1 gateways that are linked to it. After you create this gateway and link a tier-1 gateway to it, you will see the actual IP address assigned to the link on the tier-0 gateway side and on the tier-1 gateway side. The address is displayed in Additional Settings > Router Links on the tier-0 gateway page and the tier-1 gateway page. The default is 100.64.0.0/16.
- In the Forwarding Up Timer field, enter a time. The forwarding up timer defines the time in seconds that the router must wait before sending the up notification after the first BGP session is established. This timer (previously known as forwarding delay) minimizes downtime in case of fail-overs for active-active or active-standby configurations of logical routers on NSX Edge that use dynamic routing (BGP). It should be set to the number of seconds an external router (TOR) takes to advertise all the routes to this router after the first BGP/BFD session. The timer value should be directly proportional to the number of northbound dynamic routes that the router must learn. This timer should be set to 0 on single-edge node setups.
7- Click Route Distinguisher for VRF Gateways to configure a route distinguisher admin address. This is only needed for EVPN in Inline mode.
8- (Optional) Click EVPN Settings to configure EVPN.
- Select an EVPN mode. The options are:
- Inline – In this mode, EVPN handles both data plane and control plane traffic.
- Route Server – Available only if this gateway’s HA mode is active-active. In this mode, EVPN handles control plane traffic only.
- No EVPN
- If EVPN mode is Inline, select an EVPN/VXLAN VNI pool or create a new pool by clicking the menu icon (3 dots).
- If EVPN mode is Route Server, select an EVPN Tenant or create a new EVPN tenant by clicking the menu icon (3 dots).
- In the EVPN Tunnel Endpoint field, click Set to add EVPN local tunnel endpoints. For the tunnel endpoint, select an Edge node and specify an IP address. Optionally, you can specify the MTU.
9- To configure route redistribution, click Route Redistribution and Set.
Select one or more of the sources:
- Tier-0 subnets: Static Routes, NAT IP, IPsec Local IP, DNS Forwarder IP, EVPN TEP IP, Connected Interfaces & Segments. Under Connected Interfaces & Segments, you can select one or more of the following: Service Interface Subnet, External Interface Subnet, Loopback Interface Subnet, or Connected Segment.
- Advertised tier-1 subnets: DNS Forwarder IP, Static Routes, LB VIP, NAT IP, LB SNAT IP, IPSec Local Endpoint, Connected Interfaces & Segments. Under Connected Interfaces & Segments, you can select Service Interface Subnet and/or Connected Segment.

Finish 🙂